Fowsniff 打靶
前言
hash破解john,hydra,crackmapexec的使用,用户组脚本提权
得用virtual box
信息收集
1 | 110 pop3 # Post Office Protocol - Version 3 |
读网站信息,被黑了,有更多信息泄露,还有twitter,但是pastebin的信息已经看不到了,直接看的 https://raw.githubusercontent.com/berzerk0/Fowsniff/main/fowsniff.txt
1 | Is that your sysadmin? roflcopter |
说md5不安全,那么我们尝试md5哈希碰撞,先看看是什么类型的hash
1 | hash-identifier 8a28a94a588a95b80163709ab4313aa4 |
立足点
1 | sudo nc 192.168.56.103 110 |
提权
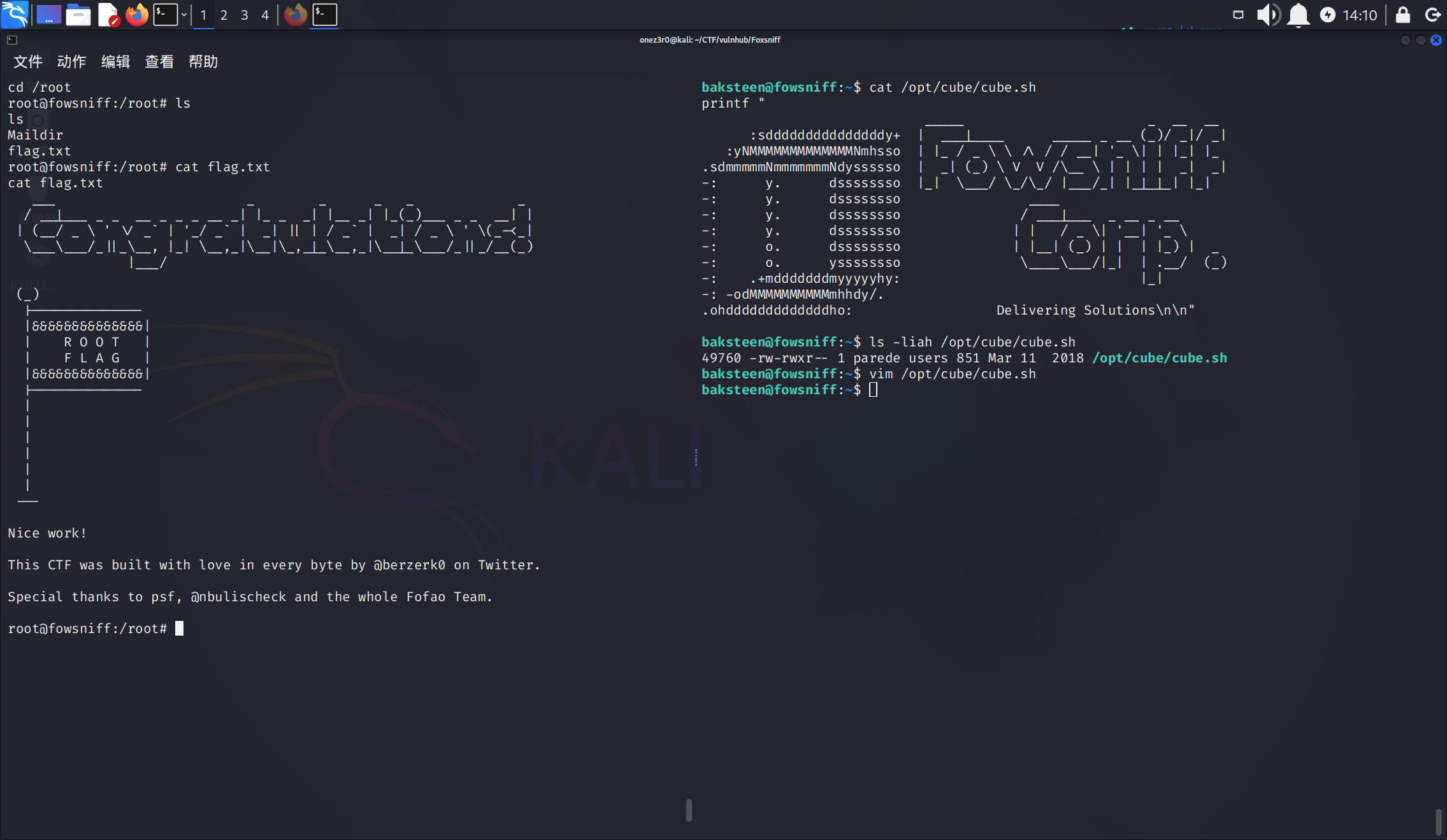
1 | find / -group users -type f 2>/dev/null |
当然这里也可以用python3 reverse shell,我这里就正常用bash弹
- 标题: Fowsniff 打靶
- 作者: OneZ3r0
- 创建于 : 2025-06-30 09:49:37
- 更新于 : 2025-07-29 18:03:58
- 链接: https://blog.onez3r0.top/2025/06/30/vulnhub-fowsniff-walkthrough/
- 版权声明: 本文章采用 CC BY-NC-SA 4.0 进行许可。